Website security is more and more a concern. Discover how to maximize online security for your business, through these answers your most pressing questions by guest author, Megha Parikh...
Guest post by Megha Parikh
Think you don't need to improve the online security for your business?
Think again!
According to 2011 SMB Threat Awareness Poll conducted by Symantec, at least 50% of Small and Medium Businesses (SMBs) assume they are insulated from cyber attacks because they are small in stature.
Contradicting their belief is the study report by Symantec which found that at least 42% of SMBs lost business information through cyber attacks and lacking online security.
So the ground reality can be aptly summarized as: businesses take online security lightly. There is a common misconception that investing in online security measures is a waste of resources and one that does not yield any profitable returns.
However, if statistics are to be referred from Heimdal Security, the world as a whole has suffered to the tune of more than $100 Billion USD due to cyber crimes and attacks. The cyber security firm further estimate approximately 230,000 malware samples to be launched into the cyberspace on a daily basis.
Here are some ways to ensure business security in the cyber space.
How To Maximize Online Security For Your Business
Whether you are a small business or one sprawling across continents, these tactics can help you save losses caused due to cyber attacks.
Ensure User Identity
Bots and DDoS attacks are primary methods for hackers to break into lesser secure networks. While there is no foolproof way to ensure user identity at check in point, security measures like captcha and prove-that-you-are-human help prevent bots and systematic hacking attempts from bearing fruit.
Set Up Firewall
Establishing a firewall is perhaps the best way a small business can fortify itself against infiltration by hackers. A firewall is like a fort wall that insulates the network and its open ports from being leveraged by hackers for unauthorized entries.
[caption id="attachment_5228" align="aligncenter" width="537"] Image credit: creativedata.net[/caption]
Image credit: creativedata.net[/caption]
A firewall will regulate the flow of information through the network without letting it get exposed at any port where the hacker can possibly make an entry. Firewalls are available as turnkey solutions which a business website can incorporate into its network for online security.
SSL Encryption
Industry stalwarts including Rick Andrews, technical director, Trust Services, Symantec recommend organization and business website owners to “use strong SSL authentication for web and data protection”
SSL encryption is a must for today’s business website owners who want to prevent any form of data infiltration from external or internal sources. A SSL certificate is basically a collection of KB sized data files that contain heavily encrypted keys to the owning organizations details like name, domain name, location and country.
The certificate is reflected on the address bar with a green padlock symbol and HTTPS in green font. It is technically referred to as extended validation which is considered a hallmark sign of website online security.
Using SSL certificates also render several additional benefits like:
- Encrypting confidential information transfer
- Building trust between buyers and sellers
- Authenticity for online banking and financial transactions
- Ensures adherence with PCI compliance
Ensure security at BYOD
BYOD is a practice which has become commonplace across all major industries. In the US along, security issues arise primarily because of unguarded personal devices like laptops and tablets.
[caption id="attachment_5229" align="aligncenter" width="599"]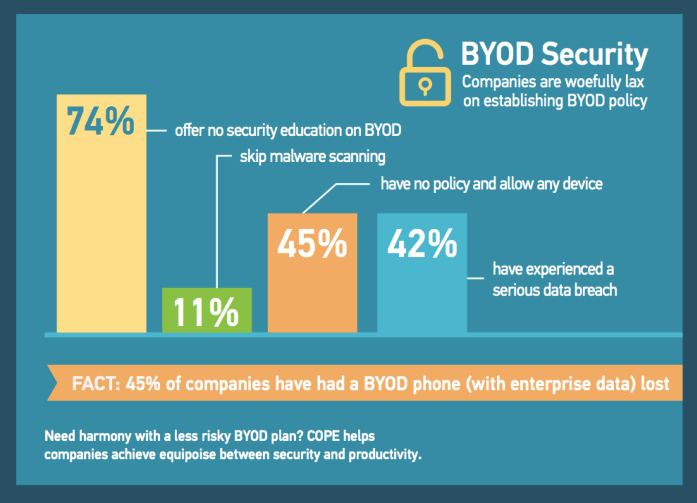 Image credit: bmc.com[/caption]
Image credit: bmc.com[/caption]
Instituting cyber security measures at BYOD end-units is the first step to prevent malware, spyware and other malicious programs from entering the system internal environment. Anti-virus and spyware protection for BYOD units can be sponsored by the organization itself or required of the user when the sign up or BYOD.
Enable CVV Verification
CVV (Card Verification Value) is a 3 digit code that is embossed behind credit and debit cards. It acts as an additional security feature in online payments where the user cannot a PIN number. CVV ensures that only authorized users who actually own the credit/debit card or those who have access to the card are carrying out the transaction.
[caption id="attachment_5230" align="aligncenter" width="449"]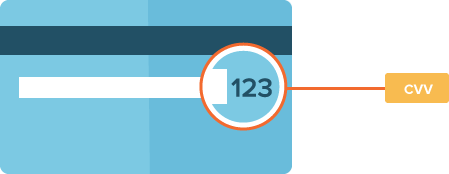 Image credit: siftscience.com[/caption]
Image credit: siftscience.com[/caption]
CVV in addition to One Time Passwords can ensure that customers are given layered online security for all online transactions where their banking credentials can possibly be compromised.
Similarly, if you are running an eCommerce store, you may also consider setting up an AVS (Address Verification System) which ensures that the billing address as given by the customer is legit and not a scam. It helps control returns and fraudulent orders.
Enlighten Employees About Cybersecurity
SolarWinds in its 2015 Federal Cybersecurity Survey has found in its survey that untrained employees are the primary security threats for federal agencies.
For any organization that takes cyber security at face value, employee training in cyber security is imperative. Employee training ensures that are standard protocols within the organization which requires employees to adhere with cyber security measures.
Such measures will include:
- Use of instant messaging solutions that are encrypted end-to-end
- Using only standardized software and web applications from trusted sources
- Layering every possible software utility with an additional level of online security
- Monitoring usage of BYOD devices and data transfer volumes
- Regular backups of data
Have a Disaster Recovery Plan
Hope is an expensive commodity. Being prepared makes is sensible.
The same goes with your organization’s IT security. Having a disaster plan that can put your organization back in track (in case of a cyber attack) is equally important to have precautionary measures.
The disaster control and recovery plan should deal with situations like:
- How to restore lost or destroyed data?
- What procedures can be used to ensure data integrity on recovery?
- How long can the disaster recovery be planned for?
- What kind of software or processes be used for disaster recovery?
A comprehensive disaster plan can be created to include routines like periodical backups, mapping old URLs to new URLs, offline server storage, seeking emergency assistance from hosting service provider, etc.
Should you outsource your website's online security?
That is a question worth pondering. In fact, some credit card processing companies do provide card processing and online transaction safety for a service cost. For a small business the cost may be exorbitant, nevertheless there are other online security consultants who can help plug the loopholes in your security process.
To begin with, you can set up your web portal with SSL certificate protection which can negate almost every existing security threat that are commonplace.
 About The Author
About The Author
Megha Parikh is a digital marketing expert and has been journeying through the world of digital marketing for more than 7 years. She especially enjoys learning about social media marketing and conversion rate optimization while exploring her social and interpersonal skills. Connect with her on Twitter and LinkedIn.
